shell实现hp刀片ilo地址配置
一、问题背景
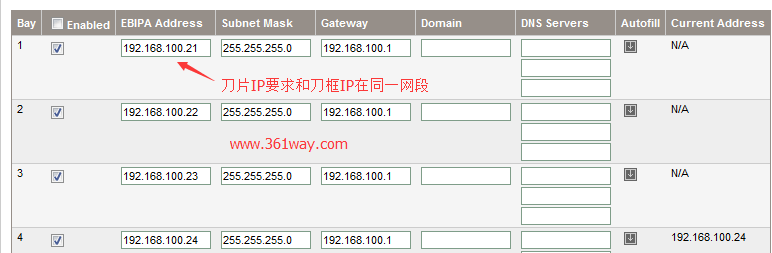
HP刀片在使用KVM远程console管理过程中,要求刀片配置的ILO地址和HP OA地址在同一网段。由于IP地址资源紧张,刀筐OA口默认配置上了地址,刀片没有配置,都是使用的时候临时配置。所以一旦物理机出现问题,想要通过远程管理口查看主机所处的状态就比较麻烦。先要通过ping工具查询预留地址是否可用。再在OA界面上进行配置,比较影响效率。
二、脚本实现
该脚本写的比较凑合,杂糅了shell、C语言、expect 三者实现的,具体代码如下:
1#!/bin/bash
2#code from www.361way.com
3#auto set the Blade ilo address
4usage( )
5{
6 echo "usage: $0 oaip username password"
7}
8if [ $# -lt 3 ]; then
9 usage
10 exit 1
11fi
12oaip=$1
13username=$2
14password=$3
15oaip=`sshpass -p$password ssh -o StrictHostKeyChecking=no $username@$oaip "SHOW OA NETWORK" |grep 'IPv4 Address:'|awk '{print $3}'`
16oamask=`sshpass -p$password ssh -o StrictHostKeyChecking=no $username@$oaip "SHOW OA NETWORK" |grep 'Netmask:'|awk '{print $2}'`
17oagate=`sshpass -p$password ssh -o StrictHostKeyChecking=no $username@$oaip "SHOW OA NETWORK" |grep 'Gateway Address:'|awk '{print $3}'`
18clear
19echo -e 'nn'
20echo '****************************'
21echo 'The Blade box information:'
22echo '****************************'
23echo IP ADDR: $oaip
24echo NETMASK: $oamask
25echo GATEway: $oagate
26mask2cdr ( )
27{
28 # Assumes there's no "255." after a non-255 byte in the mask
29 local x=${1##*255.}
30 set -- 0^^^128^192^224^240^248^252^254^ $(( (${#1} - ${#x})*2 )) ${x%%.*}
31 x=${1%%$3*}
32 echo $(( $2 + (${#x}/4) ))
33}
34cdr2mask ( )
35{
36 # Number of args to shift, 255..255, first non-255 byte, zeroes
37 set -- $(( 5 - ($1 / 8) )) 255 255 255 255 $(( (255 << (8 - ($1 % 8))) & 255 )) 0 0 0
38 [ $1 -gt 1 ] && shift $1 || shift
39 echo ${1-0}.${2-0}.${3-0}.${4-0}
40}
41addcdr=$oaip/`mask2cdr $oamask`
42echo -e 'nn'
43echo '******************************'
44echo We will scan the network
45echo And get can use ip now
46echo Please wait a moment!!!
47echo '******************************'
48fping -g $(echo `./net2ip $addcdr`)|grep 'unreachable'
49read -p "Enter can used ip for blade: " iloip
50read -p "Enter the blade bay id: " bid
51setip="set ebipa server $iloip $oamask $bid"
52setgate="set ebipa server gateway $oagate $bid"
53cat>autoexec.exp<"
54send "set ebipa server $iloip $oamask $bidn"
55expect "*bays?"
56send "YESn"
57expect "*>"
58send "set ebipa server gateway $oagate $bidn"
59sleep 2
60expect "*?"
61send "YESn"
62expect eof
63#interact
64EOF
65expect -f autoexec.exp
凑合着功能实现了,后面有时间统一使用python再实现下。
捐赠本站(Donate)
 如您感觉文章有用,可扫码捐赠本站!(If the article useful, you can scan the QR code to donate))
如您感觉文章有用,可扫码捐赠本站!(If the article useful, you can scan the QR code to donate))
- Author: shisekong
- Link: https://blog.361way.com/shell-hpoa-ilo/5566.html
- License: This work is under a 知识共享署名-非商业性使用-禁止演绎 4.0 国际许可协议. Kindly fulfill the requirements of the aforementioned License when adapting or creating a derivative of this work.