ldap用户及权限管理
openldap默认的账户是cn=Manager,dc=361way,dc=com这样的一个账户 ,其写在配置文件/etc/openldap/slapd.conf文件中,但这样的一个账户就像linux下的root一样,虽然好用,不过权限太大 。出于安全考量,我们需要根据具体应用的需要,建立只读账户或者可写用户。
一、新建管理账号
新建管理账户的方法很多,可以使用像诸如 ldapadmin、phpldapadmin、LDAP browser/editor等工具,也可以通过ldapadd 或slapadd这样的客户端工具(关于两 者的区别可以参看IBM 技术网)。这里假设以ldapadd为例,具体做法如下:
1、新建一 ldif文件,具体内容类似下面的:
1dn: cn=bbs,dc=361way,dc=com
2objectClass: person
3objectClass: shadowAccount
4objectClass: top
5cn: bbs
6sn: bbs
7uid: bbs
8userPassword:: e1NTSEF9RHpONi9jM0xvaDRpd0RzN2ROVnVKZGdxYVJ0eUg1RGU=
9structuralObjectClass: person
10entryUUID: d08e9e12-a8c9-1032-9efa-9d41910b717f
11creatorsName: cn=Manager,dc=361way,dc=com
12createTimestamp: 20130903094905Z
13entryCSN: 20130903094905Z#000001#00#000000
14modifiersName: cn=Manager,dc=361way,dc=com
15modifyTimestamp: 20130903094905Z
2、执行如下的命令操作导入:
1ldapadd -x -W -D "cn=Manager,dc=361way,dc=com" -f test.ldif
注:如果条件允许,建议还是使用图形化的客户端去操作。如delphi写的LDAPadmin就非常好用。
二、给账号设置权限
默认新建的这个账号是没有管理任何用户的权限的 ,可以用这个新建的账号登陆客户端验证。
给新建的账户赋权限也是通过修改配置文件/etc/openldap/slapd.conf来实现,具体的增加的内容如下:
1# Personal LDAP address book.
2access to dn.regex="cn=[^,]+,mail=([^,]+)@([^,]+),ou=Users,domainName=([^,]+),o=domains,dc=361way,dc=com$"
3 by anonymous none
4 by self none
5 by dn.exact="cn=bbs,dc=361way,dc=com" read
6 by dn.exact="cn=bbsadmin,dc=361way,dc=com" write
7 by dn.regex="mail=$1@$2,ou=Users,domainName=$3,o=domains,dc=361way,dc=com$" write
8 by users none
9# Allow users to change their own passwords and mail forwarding addresses.
10access to attrs="userPassword,mailForwardingAddress"
11 by anonymous auth
12 by self write
13 by dn.exact="cn=bbs,dc=361way,dc=com" read
14 by dn.exact="cn=bbsadmin,dc=361way,dc=com" write
15 by users none
16# Allow to read others public info.
17access to attrs="cn,sn,gn,givenName,telephoneNumber"
18 by anonymous auth
19 by self write
20 by dn.exact="cn=bbs,dc=361way,dc=com" read
21 by dn.exact="cn=bbsadmin,dc=361way,dc=com" write
22 by users read
23# Domain attrs.
24access to attrs="objectclass,domainName,mtaTransport,enabledService,domainSenderBccAddress,domainRecipientBccAddress,domainBackupMX,domainMaxQuotaSize,domainMaxUserNumber"
25 by anonymous auth
26 by self read
27 by dn.exact="cn=bbs,dc=361way,dc=com" read
28 by dn.exact="cn=bbsadmin,dc=361way,dc=com" write
29 by users read
30access to attrs="domainAdmin,domainGlobalAdmin,domainSenderBccAddress,domainRecipientBccAddress"
31 by anonymous auth
32 by self read
33 by dn.exact="cn=bbs,dc=361way,dc=com" read
34 by dn.exact="cn=bbsadmin,dc=361way,dc=com" write
35 by users none
36# User attrs.
37access to attrs="employeeNumber,homeDirectory,mailMessageStore,mail,accountStatus,userSenderBccAddress,userRecipientBccAddress,mailQuota,backupMailAddress,shadowAddress"
38 by anonymous auth
39 by self read
40 by dn.exact="cn=bbs,dc=361way,dc=com" read
41 by dn.exact="cn=bbsadmin,dc=361way,dc=com" write
42 by users read
43#
44# Set ACL for bbs/bbsadmin.
45#
46access to dn="cn=bbs,dc=361way,dc=com"
47 by anonymous auth
48 by self write
49 by dn.exact="cn=bbsadmin,dc=361way,dc=com" write
50 by users none
51access to dn="cn=bbsadmin,dc=361way,dc=com"
52 by anonymous auth
53 by self write
54 by users none
55#
56# Allow users to access their own domain subtree.
57# Allow domain admin to modify accounts under same domain.
58#
59access to dn.regex="domainName=([^,]+),o=domains,dc=361way,dc=com$"
60 by anonymous auth
61 by self write
62 by dn.exact="cn=bbs,dc=361way,dc=com" read
63 by dn.exact="cn=bbsadmin,dc=361way,dc=com" write
64 by dn.regex="mail=[^,]+@$1,o=domainAdmins,dc=361way,dc=com$" write
65 by dn.regex="mail=[^,]+@$1,ou=Users,domainName=$1,o=domains,dc=361way,dc=com$" read
66 by users none
67#
68# Grant correct privileges to bbs/bbsadmin.
69#
70access to dn.subtree="o=domains,dc=361way,dc=com"
71 by anonymous auth
72 by self write
73 by dn.exact="cn=bbs,dc=361way,dc=com" read
74 by dn.exact="cn=bbsadmin,dc=361way,dc=com" write
75 by dn.regex="mail=[^,]+,ou=Users,domainName=$1,o=domains,dc=361way,dc=com$" read
76 by users read
77access to dn.subtree="o=domainAdmins,dc=361way,dc=com"
78 by anonymous auth
79 by self write
80 by dn.exact="cn=bbs,dc=361way,dc=com" read
81 by dn.exact="cn=bbsadmin,dc=361way,dc=com" write
82 by users none
83#
84# Set permission for "cn=*,dc=361way,dc=com".
85#
86access to dn.regex="cn=[^,]+,dc=361way,dc=com"
87 by anonymous auth
88 by self write
89 by users none
90#
91# Set default permission.
92#
93access to *
94 by anonymous auth
95 by self write
96 by users read
如上面示例中就定义了两个用户,一个是只读用户cn=bbs,dc=361way,dc=com和一个可写用户cn=bbsadmin,dc=361way,dc=com 以及这两个用户对所列的字段、正则 匹配的用户有相应的权限 。
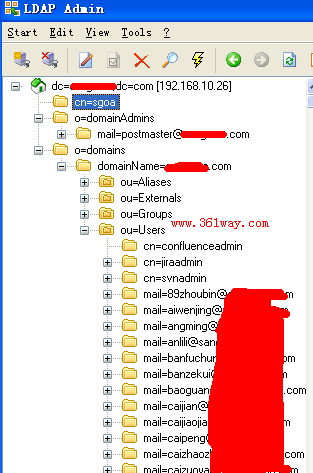
更改完该配置文件后重启ldap服务,再重新登陆查看,如下
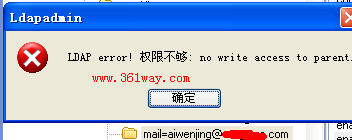
以上这个只读账户如果想删除相应的内容就会提示没有权限 :
捐赠本站(Donate)
 如您感觉文章有用,可扫码捐赠本站!(If the article useful, you can scan the QR code to donate))
如您感觉文章有用,可扫码捐赠本站!(If the article useful, you can scan the QR code to donate))
- Author: shisekong
- Link: https://blog.361way.com/ldap-adduser-grants/2825.html
- License: This work is under a 知识共享署名-非商业性使用-禁止演绎 4.0 国际许可协议. Kindly fulfill the requirements of the aforementioned License when adapting or creating a derivative of this work.