再看SecureCRT密码解密
在《python3解密SecureCRT的密码》篇中提到了利用python进行SecureCRT加密后的密文进行解密的方法。但在不同版本的SecureCRT中%APPDATA%\VanDyke\Config\Sessions\example.com.ini配置中对应的password可能是不一样的,有些密码存储在password项,有些存储的是Password V2项,具体类似如下:
1S:"Password"=u17cf50e394ecc2a06fa8919e1bd67cf0f37da34c78e7eb87a3a9a787a9785e802dd0eae4e8039c3ce234d34bfe28bbdc
2S:"Password V2"=02:7b9f594a1f39bb36bbaa0d9688ee38b3d233c67b338e20e2113f2ba4d328b6fc8c804e3c02324b1eaad57a5b96ac1fc5cc1ae0ee2930e6af2e5e644a28ebe3fc
这两者之间的加解密方法是有区别的。具体一般以SecureCRT 7.3.3版本进行分界。之前的版本一般会使用password加密算法,之后的一般使用password v2算法。
一、Password算法
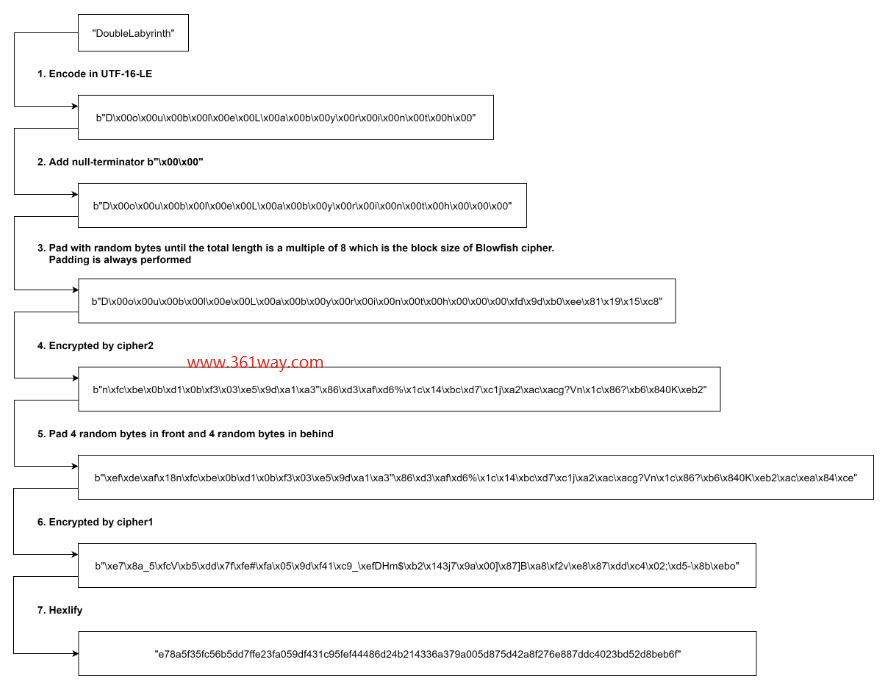
这个也是开篇链接中我之前的博文中提到的,其使用的是2次Blowfish-CBC加密,这里记录为cipher1和cipher2。两者使用的初始公共因子是8位的16进制的0,具体表示如下:
1uint8_t IV[8] = {
2 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00
3}
cipher1 使用的key是:
1uint8_t Key1[16] = {
2 0x24, 0xa6, 0x3d, 0xde, 0x5b, 0xd3, 0xb3, 0x82,
3 0x9c, 0x7e, 0x06, 0xf4, 0x08, 0x16, 0xaa, 0x07
4}
cipher2 使用的key是:
1uint8_t Key2[16] = {
2 0x5f, 0xb0, 0x45, 0xa2, 0x94, 0x17, 0xd9, 0x16,
3 0xc6, 0xc6, 0xa2, 0xff, 0x06, 0x41, 0x82, 0xb7
4}
其加密过程如下:
同样对应的其解密过程如下:
二、password v2算法
password v2使用的是AES256-CBC 算法,其初始因子是16位16进制的0,具体如下:
1uint8_t IV[16] = {
2 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
3 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00
4}
其使用的32位key是:
1uint8_t Key[32] = {
2 0xe3, 0xb0, 0xc4, 0x42, 0x98, 0xfc, 0x1c, 0x14,
3 0x9a, 0xfb, 0xf4, 0xc8, 0x99, 0x6f, 0xb9, 0x24,
4 0x27, 0xae, 0x41, 0xe4, 0x64, 0x9b, 0x93, 0x4c,
5 0xa4, 0x95, 0x99, 0x1b, 0x78, 0x52, 0xb8, 0x55
6}
对应的加密过程是:
对应的解密过程如下:
三、解密代码
这里还是以python为例,对应的即可以解密password也可以解密password v2的代码如下:
1#!/usr/bin/env python3
2import os
3from Crypto.Hash import SHA256
4from Crypto.Cipher import AES, Blowfish
5class SecureCRTCrypto:
6 def __init__(self):
7 '''
8 Initialize SecureCRTCrypto object.
9 '''
10 self.IV = b'\x00' * Blowfish.block_size
11 self.Key1 = b'\x24\xA6\x3D\xDE\x5B\xD3\xB3\x82\x9C\x7E\x06\xF4\x08\x16\xAA\x07'
12 self.Key2 = b'\x5F\xB0\x45\xA2\x94\x17\xD9\x16\xC6\xC6\xA2\xFF\x06\x41\x82\xB7'
13 def Encrypt(self, Plaintext : str):
14 '''
15 Encrypt plaintext and return corresponding ciphertext.
16 Args:
17 Plaintext: A string that will be encrypted.
18 Returns:
19 Hexlified ciphertext string.
20 '''
21 plain_bytes = Plaintext.encode('utf-16-le')
22 plain_bytes += b'\x00\x00'
23 padded_plain_bytes = plain_bytes + os.urandom(Blowfish.block_size - len(plain_bytes) % Blowfish.block_size)
24 cipher1 = Blowfish.new(self.Key1, Blowfish.MODE_CBC, iv = self.IV)
25 cipher2 = Blowfish.new(self.Key2, Blowfish.MODE_CBC, iv = self.IV)
26 return cipher1.encrypt(os.urandom(4) + cipher2.encrypt(padded_plain_bytes) + os.urandom(4)).hex()
27 def Decrypt(self, Ciphertext : str):
28 '''
29 Decrypt ciphertext and return corresponding plaintext.
30 Args:
31 Ciphertext: A hex string that will be decrypted.
32 Returns:
33 Plaintext string.
34 '''
35 cipher1 = Blowfish.new(self.Key1, Blowfish.MODE_CBC, iv = self.IV)
36 cipher2 = Blowfish.new(self.Key2, Blowfish.MODE_CBC, iv = self.IV)
37 ciphered_bytes = bytes.fromhex(Ciphertext)
38 if len(ciphered_bytes) <= 8:
39 raise ValueError('Invalid Ciphertext.')
40 padded_plain_bytes = cipher2.decrypt(cipher1.decrypt(ciphered_bytes)[4:-4])
41 i = 0
42 for i in range(0, len(padded_plain_bytes), 2):
43 if padded_plain_bytes[i] == 0 and padded_plain_bytes[i + 1] == 0:
44 break
45 plain_bytes = padded_plain_bytes[0:i]
46 try:
47 return plain_bytes.decode('utf-16-le')
48 except UnicodeDecodeError:
49 raise(ValueError('Invalid Ciphertext.'))
50class SecureCRTCryptoV2:
51 def __init__(self, ConfigPassphrase : str = ''):
52 '''
53 Initialize SecureCRTCryptoV2 object.
54 Args:
55 ConfigPassphrase: The config passphrase that SecureCRT uses. Leave it empty if config passphrase is not set.
56 '''
57 self.IV = b'\x00' * AES.block_size
58 self.Key = SHA256.new(ConfigPassphrase.encode('utf-8')).digest()
59 def Encrypt(self, Plaintext : str):
60 '''
61 Encrypt plaintext and return corresponding ciphertext.
62 Args:
63 Plaintext: A string that will be encrypted.
64 Returns:
65 Hexlified ciphertext string.
66 '''
67 plain_bytes = Plaintext.encode('utf-8')
68 if len(plain_bytes) > 0xffffffff:
69 raise OverflowError('Plaintext is too long.')
70 plain_bytes = \
71 len(plain_bytes).to_bytes(4, 'little') + \
72 plain_bytes + \
73 SHA256.new(plain_bytes).digest()
74 padded_plain_bytes = \
75 plain_bytes + \
76 os.urandom(AES.block_size - len(plain_bytes) % AES.block_size)
77 cipher = AES.new(self.Key, AES.MODE_CBC, iv = self.IV)
78 return cipher.encrypt(padded_plain_bytes).hex()
79 def Decrypt(self, Ciphertext : str):
80 '''
81 Decrypt ciphertext and return corresponding plaintext.
82 Args:
83 Ciphertext: A hex string that will be decrypted.
84 Returns:
85 Plaintext string.
86 '''
87 cipher = AES.new(self.Key, AES.MODE_CBC, iv = self.IV)
88 padded_plain_bytes = cipher.decrypt(bytes.fromhex(Ciphertext))
89 plain_bytes_length = int.from_bytes(padded_plain_bytes[0:4], 'little')
90 plain_bytes = padded_plain_bytes[4:4 + plain_bytes_length]
91 if len(plain_bytes) != plain_bytes_length:
92 raise ValueError('Invalid Ciphertext.')
93 plain_bytes_digest = padded_plain_bytes[4 + plain_bytes_length:4 + plain_bytes_length + SHA256.digest_size]
94 if len(plain_bytes_digest) != SHA256.digest_size:
95 raise ValueError('Invalid Ciphertext.')
96 if SHA256.new(plain_bytes).digest() != plain_bytes_digest:
97 raise ValueError('Invalid Ciphertext.')
98 return plain_bytes.decode('utf-8')
99if __name__ == '__main__':
100 import sys
101 def Help():
102 print('Usage:')
103 print(' SecureCRTCipher.py <enc|dec> [-v2] [-p ConfigPassphrase] <plaintext|ciphertext>')
104 print('')
105 print(' <enc|dec> "enc" for encryption, "dec" for decryption.')
106 print(' This parameter must be specified.')
107 print('')
108 print(' [-v2] Encrypt/Decrypt with "Password V2" algorithm.')
109 print(' This parameter is optional.')
110 print('')
111 print(' [-p ConfigPassphrase] The config passphrase that SecureCRT uses.')
112 print(' This parameter is optional.')
113 print('')
114 print(' <plaintext|ciphertext> Plaintext string or ciphertext string.')
115 print(' NOTICE: Ciphertext string must be a hex string.')
116 print(' This parameter must be specified.')
117 print('')
118 def EncryptionRoutine(UseV2 : bool, ConfigPassphrase : str, Plaintext : str):
119 try:
120 if UseV2:
121 print(SecureCRTCryptoV2(ConfigPassphrase).Encrypt(Plaintext))
122 else:
123 print(SecureCRTCrypto().Encrypt(Plaintext))
124 return True
125 except:
126 print('Error: Failed to encrypt.')
127 return False
128 def DecryptionRoutine(UseV2 : bool, ConfigPassphrase : str, Ciphertext : str):
129 try:
130 if UseV2:
131 print(SecureCRTCryptoV2(ConfigPassphrase).Decrypt(Ciphertext))
132 else:
133 print(SecureCRTCrypto().Decrypt(Ciphertext))
134 return True
135 except:
136 print('Error: Failed to decrypt.')
137 return False
138 def Main(argc : int, argv : list):
139 if 3 <= argc and argc <= 6:
140 bUseV2 = False
141 ConfigPassphrase = ''
142 if argv[1].lower() == 'enc':
143 bEncrypt = True
144 elif argv[1].lower() == 'dec':
145 bEncrypt = False
146 else:
147 Help()
148 return -1
149 i = 2
150 while i < argc - 1:
151 if argv[i].lower() == '-v2':
152 bUseV2 = True
153 i += 1
154 elif argv[i].lower() == '-p' and i + 1 < argc - 1:
155 ConfigPassphrase = argv[i + 1]
156 i += 2
157 else:
158 Help()
159 return -1
160 if bUseV2 == False and len(ConfigPassphrase) != 0:
161 print('Error: ConfigPassphrase is not supported if "-v2" is not specified')
162 return -1
163 if bEncrypt:
164 return 0 if EncryptionRoutine(bUseV2, ConfigPassphrase, argv[-1]) else -1
165 else:
166 return 0 if DecryptionRoutine(bUseV2, ConfigPassphrase, argv[-1]) else -1
167 else:
168 Help()
169 exit(Main(len(sys.argv), sys.argv))
该脚本需要依赖pycryptodome模块,该模块是一个加解密算法的模块包,该模块是pyCyrpto模块的延续。由于pyCyrpto在python3.4已停止更新。后面新的版本就变成了pycryptodome。
捐赠本站(Donate)
 如您感觉文章有用,可扫码捐赠本站!(If the article useful, you can scan the QR code to donate))
如您感觉文章有用,可扫码捐赠本站!(If the article useful, you can scan the QR code to donate))
- Author: shisekong
- Link: https://blog.361way.com/securecrt-password-ini/6345.html
- License: This work is under a 知识共享署名-非商业性使用-禁止演绎 4.0 国际许可协议. Kindly fulfill the requirements of the aforementioned License when adapting or creating a derivative of this work.